Access to information is becoming increasingly important in this digital age. As businesses gain access to more valuable information through their Network Services, threats to network security, hacks, data breaches, and cyberattacks are becoming more common. Information security is critical for the success of a business. This makes cybersecurity a chief concern.
Network security tools protect your data from cyberattacks while also ensuring authorized users have access to perform their tasks effectively. Computer network security is made up of different elements of cybersecurity, including a variety of applications, configurations, and tools that are used to protect your network’s integrity from unauthorized use.
Network security attacks can take many forms and originate from a variety of sources. Network security technologies are intended to target specific threats while preventing disruption or damage to your network’s underlying infrastructure.
Effective network security acts as a gatekeeper, preventing unauthorized access, modification, misuse, or alteration of a computer, etc. Understanding the fundamentals of security on the internet will enable you and your company to maintain a secure and dependable working environment.
In this article, we’ll define network security, explain why it’s important for your business, and discuss which network security types may apply to you.
Contents
- 1 What is network security?
- 2 How does network security work?
- 3 Why is network security important?
- 4 Types of network security protection
- 5 Benefits of network security
- 6 Network security and the cloud
- 7 Network security for businesses and consumers
- 8 Network
security tools and techniques
- 8.1 1. Control of access
- 8.2 2. Anti-malware software
- 8.3 3. Application security
- 8.4 4. Data loss prevention (DLP)
- 8.5 5. Email security
- 8.6 6. Endpoint security
- 8.7 6. Firewalls
- 8.8 7. Intrusion Prevention Systems
- 8.9 8. Anomaly Detection
- 8.10 9. Network Segmentation
- 8.11 10. Security Information and Event Management (SIEM)
- 8.12 11. Virtual Private Network (VPN)
- 8.13 12. Web Security
- 8.14 13. Wireless Security
- 9 Network security applications
- 10 FAQs
What is network security?
The measures taken by any enterprise or organization to ensure the cybersecurity of its computer network and data using both hardware and software systems are referred to as “Network Security.”
Network security encompasses a wide range of cyber security solutions, technologies, devices, and processes designed to safeguard computer networks and data integrity, confidentiality, and accessibility. Computer and network security solutions protect systems from a variety of vulnerabilities, including:
1. Users
2. Addresses
3. Information
4. Devices
5. Utilization
Today’s network architecture is complex, with an ever-changing environment of threats on the internet. Attackers are constantly looking for and exploiting vulnerabilities in network security devices, data, applications, users, and locations. As a result, regardless of size, industry, or infrastructure, every organization requires some level of cyber security management solutions in place to protect itself from the ever-growing landscape of network security threats.
Computer networks are used in daily transactions and communication within government, private, and corporate organizations that require security. Safeguards are critical when a few minutes of downtime in network and security can cause extensive disruption and massive damage to an organization’s reputation.
Numerous network security management tools and applications are available today that address both individual cyber threat types and regulatory non-compliance. The most common and straightforward methods of cyber tools are a unique name, a password, and a firewall on a computer.
Network security acts as a vulnerability manager, consisting of the following components:
- Security: The user must be able to configure their devices and networks correctly.
- Detection: The user must be notified if the configuration has changed or if there is a problem with the network traffic.
- Reaction: Once the problems have been identified, the user must respond to them and return to a safe position as soon as possible.
How does network security work?
When it comes to network security in an organization, cyber security companies have numerous layers to consider. Because types of network attacks can occur at any layer of the network security layers model, your cybersecurity hardware, software, and policies must be designed to cover all bases.
The basic principle of network security is to protect large amounts of stored data and networks in layers that ensure the bedding of rules and regulations that must be acknowledged before any activity on the data is performed.
These levels are as follows:
- Physical
- Technical
- Management and administration

Here’s a rundown of the various types of network security and how each control works.
1. Physical network security
Physical security controls are the network security basics intended to prevent unauthorized personnel from physically accessing network components such as routers and cabling cabinets. Locks, biometric authentication, and other devices that control access are essential in any organization.
2. Technical network security
Data that is stored on the network or in transit across, into, or out of the network is protected by technical security controls. Technical network security services protect in two ways: they must protect data from cyber security attacks and systems from unauthorized personnel while protecting against malicious employee activity.
3. Administrative network protection
This level of network security safeguards user behavior, such as how permission is granted and how the authorization process works. This also ensures the level of sophistication required to protect itself from all network attack types. This level also suggests infrastructure modifications that are required.
Network security employs multiple layers of protection at the network’s edge and between networks. For cybersecurity importance, all security layers carry out some strategies and adhere to specific policies. Only authorized users will access network resources, while unauthorized users will be prevented from conducting exploits and malicious activities.
Why is network security important?
Network security protects a network’s integrity from unauthorized access and threats. Cyber network security administrators are responsible for implementing various defensive measures to protect their networks from potential security threats. The following are the reasons why network security is key.
- Because of the growing number of hackers attempting to infect devices, maintaining a high level of data protection makes for the importance of cyber security
- The primary goal of network security is to prevent security breaches and network threats in the networking environment while also limiting the risk of fraud and destruction.
- Protecting corporate resources with a reliable computer security system and wireless security is a major consideration for cybersecurity. The current operations include not only computer operating systems but also data stored across the network.
- The company’s data is just as important and valuable as its other physical assets. Network security is concerned with accuracy, confidentiality, and secure access to sensitive data.
- Every business is responsible for taking appropriate security precautions to ensure the safety of its operations. Because technology is used for most of the operational business, specific security tools, policies, and techniques must be developed to ensure that the company’s network security requirements are met.
- Compliance with WiFi security requirements and standards safeguards both corporate resources and responsibility from certain types of cyber threats.
- Even a minor network threat can cause organizations to be disrupted, data to be compromised, and overall efficiency to suffer.
- When network security is enforced, the impact of security vulnerabilities is reduced.
Types of network security protection
The following are the various types of cyber security or network security protection:
1. Network segmentation
By separating the infrastructure into discrete confined pieces, network segmentation successfully eliminates the design flaw and makes it extremely difficult for intruders to damage the entire system.
2. Firewall
A firewall and different types of firewalls examine a computer’s inbound and outbound traffic for evidence of malicious behavior. If the network firewall detects anything suspicious, it will immediately stop approaching its target.

Network Firewall
3. Data loss prevention
Data loss prevention (DLP) aims to detect and mitigate network attacks like data leakage, theft, and abuse through computer security threats, attacks,and unauthorized usage.
4. Security for hyperscale networks
Hyperscale computing is the most efficient among cyber security types to achieve certain business goals, such as big data analytics and cloud computing capabilities.
5. Sandboxing
A sandbox is a virtual environment that isolates a specific system. The environment simulates the computer in its settings. This protects your system and connections in the event of a data breach.
6. Intrusion detection and prevention systems
With an intrusion prevention system (IPS) and an intrusion detection system (IDS):
- Examine network traffic for potential threats.
- Rules established by the network administrator
There are also many types of intrusion detection systems.
7. Biometric system
Biometric technology measures biological characteristics such as fingerprint recognition, face detection, and retina scanning.
8. Verification
When a user logs into a network system, user authorization is the first step in validating that user’s information.
9. Email safety
Traditional email security measures such as password protection and secure communications are included, as well as modern concepts such as spam blocking and scam protection.
10. VPN remote access
A remotely accessible virtual private network (VPN) encrypts all communication sent and received by users working remotely, allowing them to access and use files and data stored in the company data center securely.

Benefits of network security
There are network controls, tools, and devices available from cybersecurity companies to assist your organization in protecting sensitive information, its overall performance, reputation, and even its ability to stay in business. If there is a vulnerability in cyber security, an effective network security protocol is important for:
1. Continued operational capability
Companies that are victims of these types of attacks in network security are frequently crippled from within, unable to address customer needs or deliver services effectively. Similarly, networks play a significant role in internal company processes. When they are attacked, those processes may halt, hampering an organization’s ability to conduct business or even resume normal operations.
2. Intact reputation
The negative impact a network breach can have on your company’s reputation is even more damaging. Given the rising tide of identity theft and other risks associated with personal information theft, many customers are already hesitant to share data with businesses. In the event of any type of network security attack, many of these customers are likely to abandon the service in favor of more secure alternatives.
It’s easy to see what’s at stake when it comes to network security:
- Loss or corruption of valuable data, significant disruption to customer service and internal processes, and reputational damage that may last long after other damages have been repaired.
- Indeed, it has been suggested that 66 percent of small businesses would be forced to shut down (temporarily or permanently) following a data breach. Even larger, more established companies may be unable to reclaim their former prominence.
Dependable types of network security software and hardware, combined with the appropriate policies and strategies about cyber security, ensure that when cyberattacks occur, their impact is minimized.
Network security and the cloud
The cloud is the necessity of the hour. Every company wants to expand its data storage capabilities so that it can be easily maintained, shared, and accessed by its employees. And since physical storage mediums are difficult to manage and eventually fail, an increasing number of businesses are outsourcing their data and computing needs to cloud service providers.
Because a single cloud service serves multiple organizations, security breaches or other information security threats or types of cyber security attacks can have far-reaching consequences, potentially jeopardizing millions of records. This is why cloud network security is concerned with safeguarding the networks, servers, applications, and data that comprise the cloud computing ecosystem.
The factors that make the cloud so powerful also make it difficult to secure:
- While adding new assets to a cloud network, these assets tend to appear and disappear as a result of technologies such as autoscaling and serverless computing.
- Because of the ease of network deployment and rapid rate of change, security teams struggle to maintain a complete picture of their cloud environment.
Keeping in mind these fundamentals of networking security and the cloud, cloud providers create hybrid infrastructures in which their internal network can securely interact with third-party servers. In addition, various cloud providers have employed security control strategies to manage network security.
Because non-IT employees’ human errors cause the majority of cyberattacks, cloud security professionals sometimes create or provide security software or network and information security training to ensure their customers and coworkers use the most up-to-date security computer best practices for cryptography and network security to reduce the possibility of accidental breaches.
Both providers and clients who use their resources bear responsibility for cloud security services in network security. The provider has to protect the data and infrastructure, while clients must access their data using secure methods such as multifactor authentication and strong passwords—the same methods used to achieve their security goals in cryptography and network security.
Network security for businesses and consumers
Digitization is a must in today’s business. As more businesses go digital, network security in computer networks and vulnerability management tools are at the top of every operations manager’s priority list.
1. Information security
Secure and dependable cybersecurity software safeguards not only the interests and operations of the organization but also any client or customer who exchanges cybersecurity website information with the organization and the general public.
2. Damage repair costs
The global cost of dealing with damage from information security attacks reached US$6 trillion by 2021, with the average cause of a cyberattack costing more than US$1 million.
As a result, any organization that works with networked data and systems should prioritize cybersecurity technology. For example, learn the difference between antivirus and firewall software and about cryptography in network security.
The following are the top advantages that a company stands to gain from improved network security:
1. Builds trust
Network security increases client and consumer confidence while protecting your company from a security breach’s reputational and legal consequences.
2. Reduces risk
The right network security solution will assist your company in remaining compliant with business and government regulations and minimizing the business and financial impact of a breach if one occurs.
3. Safeguards confidential information
Cybersecurity works to protect information and data that is shared across a network from web security threats.
4. A safer modern workplace
Effective network security provides many levels of security to scale with your growing business by allowing employees and clients to engage securely with your business.
Network security tools and techniques
To combat the potential unauthorized entry of an outside bug into your system, the following cyber security tools and techniques are designed to assist you:
1. Control of access
Restricting user access and resources to parts of the network
2. Anti-malware software
Detect and prevent the spread of malicious programs.
3. Application security
Application security establishes security parameters for any applications that may be relevant to network security.
4. Data loss prevention (DLP)
Prevent employees and other users from misusing and potentially compromising sensitive data or from allowing such data to leave the network.
5. Email security
Identify and block attacks and prevent the sharing of vital data.
6. Endpoint security
Extra layer of protection between remote devices and business networks.
6. Firewalls
Manage network traffic with firewalls, allowing authorized traffic while blocking non-authorized traffic. This is firewall security.
7. Intrusion Prevention Systems
Scan and analyze network traffic/packets to quickly identify and respond to various attacks.
8. Anomaly Detection
Analyze your network so that you are notified quickly enough to respond when breaches occur.
9. Network Segmentation
Allow suitable traffic access while restricting traffic from doubtful sources.
10. Security Information and Event Management (SIEM)
Provide responders with the information they need to act quickly.
11. Virtual Private Network (VPN)
Authenticated communication between secure networks and endpoint devices.
12. Web Security
Ensure secure web browsing when connected to an internal network.
13. Wireless Security
Prevent threat actors from gaining access.
Network security applications
The following are some cyber security applications:
- Defense Pro: This mitigation device guards against network and application downtime.
- Defense Flow: Defense Flow can detect multivendor attacks and help mitigate it.
- App Wall: We use App Wall to ensure critical applications’ timely, dependable, and secure delivery.
- Emergency Response Team: Companies that face denial of service attacks use the Emergency Response Team, which provides twenty-four-seven security services.
- Inflight: Inflight is a monitoring application that captures all user transactions from inflight network traffic and delivers real-time intelligence to business applications.
- Cloud WAF Service: The application provides web application security and protects against evolving threats.
- Cloud DDOS Protection Service: Cloud DDOS protection service provides enterprise-grade DDOS protection in the cloud.
- Cloud Malware Protection Service: Cloud malware protection service detects unknown malware based on their unique behavior patterns using patented algorithms on data collected from a community of two million users, and this data is analyzed to provide a defense to organizations against malware.
FAQs
1. What is network access control?
Network access control is a security solution in a network security model that employs a set of protocols to keep unauthorized users and devices out of a private network or to grant restricted access to devices that adhere to network security policies.
Access control network security is in charge of network management and security, which includes implementing security policies, ensuring compliance, and managing network access control.
Access control in network security operates on wired and wireless networks by identifying various network-connected devices. Administrators will determine the protocols that will decide how devices and users are authorized for the appropriate level of authorization when setting up a NAC intrusion prevention system.
2. What are the basics of network security?
Introduction to cybersecurity practices basics of cybersecurity preventing unauthorized users or cyber security threats from accessing computer networks and their associated devices is known as network security. The need for cyber security entails physically protecting network servers and devices from types of cyber security threats and securing the digital network. There are three major areas of focus in network security:
Protection: Any security tools or policies designed to prevent network security intrusion are included.
Detection: The resources allow you to analyze network traffic and quickly identify problems before they cause harm.
Response: The ability to respond to identified network security threats and resolve them as quickly as possible.
3. What are the 5 network topologies?
A. Bus Network Topology
There is a backbone, which is a large cable that runs through the network, and computers or nodes are connected to it by tapping into the wire.

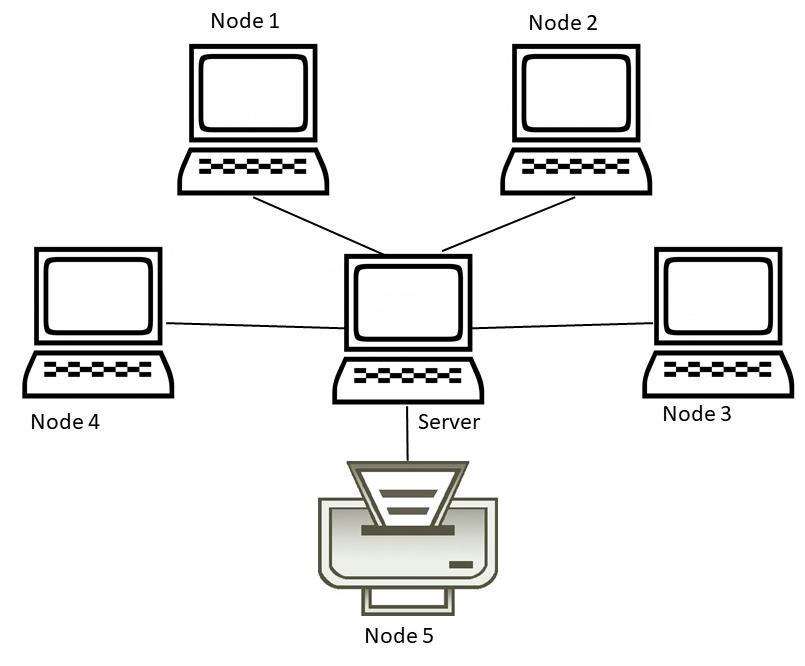
B. Star topology
A central server to which all nodes are linked, and the central server handles data transactions between the nodes
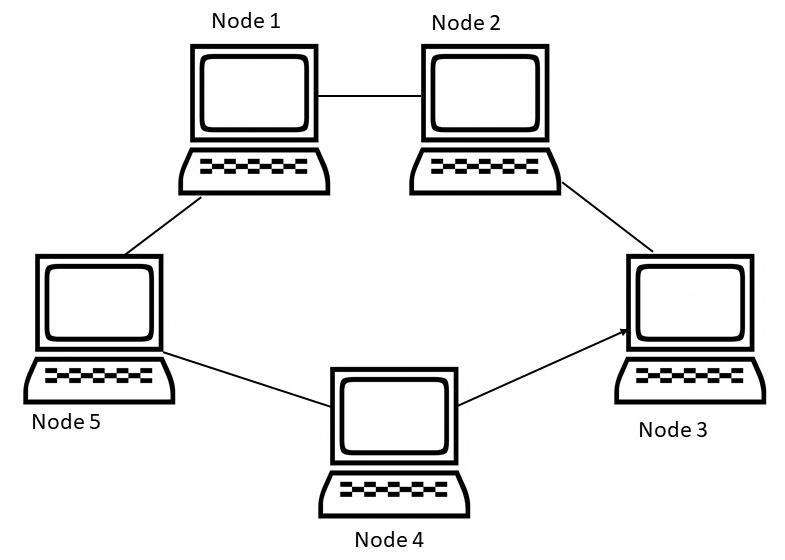
C. Ring topology
Each computer is linked to the next in order for data transmission to occur until the ends meet. There is no central server or switch to handle data transmission between the nodes.
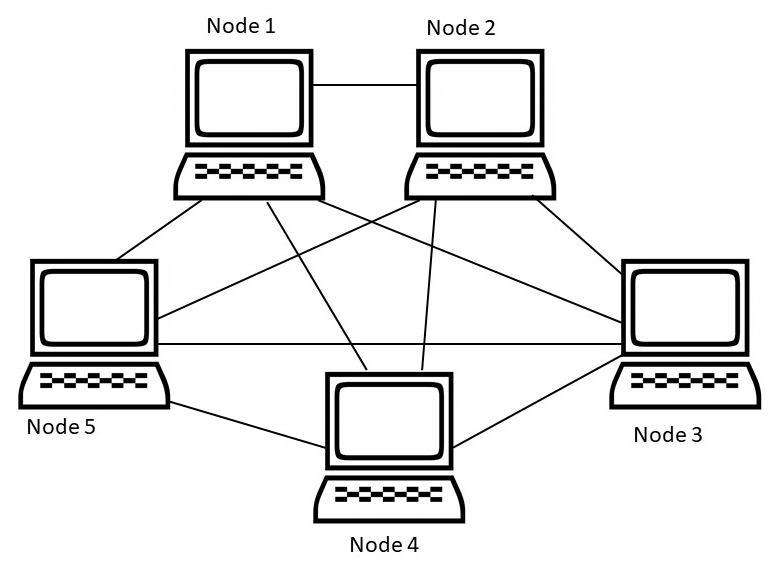
D. Mesh topology
All devices on the network will be directly connected to one another.
E. Tree topology
The network is divided into hierarchies that are linked together by a central server, which is linked to others by another server on top of it.

4. What are the 4 types of networks?
Networks are classified into four types:
A. PAN (Personal Area Network)
PAN enables data exchange between nearby devices (usually in the same room). There are two physical transmission techniques for this: USB and FireWire.
B. LAN (Local Area Network)
LAN is an abbreviation for Local Area Network. It is a collection of computers belonging to the same organization and linked together by a network in a small geographical area.
C. MAN (Metropolitan Area Network)
MANs interconnect various geographically close LANs at high speeds (a few kilometers at most).
D. WAN (Wide Area Network)
A WAN (Wide Area Network) connects multiple LANs over long distances.















