A secure, agile, real-time cloud platform that allows you to tune individual components throughout the customer and employee experience is mandatory. And it all leads to a scalable and differentiated experience. Security professionals are no longer solely responsible for cybersecurity. Instead, all digital and technology leaders need to make cybersecurity a top priority because people who pose threats are getting smarter, more creative, and more likely to work together.
Contents
What is cloud security?
Source: Cloud security
Cloud security is a set of policies, controls, procedures, and technologies that work together to protect cloud-based applications, data, and infrastructure. These security measures are configured to protect cloud data, support regulatory compliance, protect customer privacy, and establish authentication rules for individual users and devices. In addition, these rules can be configured and managed in one place. It reduces administrative overhead and allows IT teams to focus on other areas of the business. How you provide cloud security depends on your individual cloud provider or the cloud security solution you have deployed. However, the implementation of cloud security processes must be a shared responsibility between the business owner and the solution provider.
Trends in Cloud Security to Watch out for in 2022
Cloud environments are protected by a variety of security measures but are vulnerable if not properly configured. Monitoring new cloud security trends can help protect your cloud environment from data breaches.
SDLC and DevSecOps within the cloud
DevSecOps is a methodology that integrates security protocols into all phases of the SDLC process. This makes it convenient to address the threat during the SDLC life cycle. DevOps and security teams need to work together to achieve large-scale digital transformation and security.
Cloud Security Posture Management (CSPM)
It is a market segment of IT security tools designed to identify cloud misconfigurations and compliance risks. An important purpose of CSPM programming is to continuously monitor the cloud infrastructure for gaps in the enforcement of security policies.
Increase in the need for centralized platforms
Cloud-native applications are becoming more and more important when working on cloud platforms. These applications are specially designed to work in the cloud. In addition, cloud-native applications take advantage of the speed and efficiency of centralized platforms.
Lack of consensus
The government has been working on implementing rules and regulations with policies to ensure proper cloud security. Users are making a lot of investments to ensure proper security. As the level of cybercrime increases, organizations need to invest time and care to adhere to regulations.
Zero trust model
The zero-trust model provides security by preventing anyone from accessing the data until the identity is authenticated. This allows users to access only the information to which they have access. By providing restricted access, you reduce the chance of data breaches.
How Can We Cope With These Trends in Cloud Security?
For business owners and IT professionals, cloud computing is a major advance in efficiency and supportability. But like the big changes in IT, the cloud carries many new security risks. No matter your business’s size, you need a dedicated security team. According to the previous annual report, the DevOps team should be considered DevSecOps. Organizations need to incorporate security, privacy, policies, and control into DevOps processes and cultures to share security responsibilities across IT organizations. This is especially true in a distributed environment where hardware and software are integrated and constantly changing. One of the main benefits of cloud computing is the ability to scale IaaS products conveniently. For example, if your company’s web traffic doubles in a month, cloud providers will increase memory and processing power to maintain performance consistency. However, this has additional security implications and should be monitored to ensure the health of all integrated systems.
How does the cloud security market look?
Increasing numbers of security breaches and cyberattacks, as well as our obligation to comply with regulatory and privacy laws, are contributing to the growth of the cloud security market ecosystem. Enterprises are moving their infrastructure to the cloud to reduce hardware costs and deliver features such as scalability, agility, speed, and cost-effectiveness. The service provider hosts all infrastructure and capabilities in cloud deployment mode. These are provided to the organization as needed and can be expanded as needed. The Asia-Pacific (APAC) region includes emerging economies such as Australia, South Korea, and Japan with developed security infrastructure. Machine learning (ML), the Internet of Things (IoT), big data analytics, and artificial intelligence (AI) are new methods being deployed in the region. Small and medium-sized enterprises are rapidly adopting cloud-based solutions to manage their enterprise data. Despite the growing importance of SMEs in this region, they are most affected by cyber and malware attacks owing to budgetary constraints and resource shortages. The cloud security market trends study includes an in-depth competitive analysis of these key players and their profiles, recent developments, and key market strategies.
Market Drivers
- Growing awareness of cybercrimes
- Generation of new cyberattacks
- Upthrust in the use of cloud-based solutions
- Upsurge in BYOD and CYOD trends to increase the demand for cloud security
Market Restraints
- Distrust and weak collaboration among companies and cloud security service providers
Opportunities
- Increase in the government initiatives to support smart infrastructure projects
- Securing online payment applications, and social media
Challenges
- Lack of awareness among enterprises due to the complexities of cloud computing models
- COVID-19 pandemic-driven market dynamics and factor analysis
How Does the Future Look for Cloud Security?
There are two types of security techniques. Some people recognize an attack and react to it, which is called reactive security features. Then there are people who can actually anticipate a dangerous event before it happens and intervene to prevent it. These are called predictive safety features. Predictive security is the future of cloud security. Predictive security is emphasized by the sophisticated web of artificial intelligence (AI) and machine learning (ML) technologies. As one security expert says, the threat is a rabbit, while a person/company is a turtle. It may not be possible to keep up with the rapid onslaught and vast amounts of enemy attacks that attack the network, but AI and ML will identify them early and provide response strategies to neutralize large-scale threats. Another advantage of the new AI cybersecurity model is understanding the context. This reduces the number of false positives that consume security professionals’ time and cause excessive pressure and frustration in large organizations. In this sense, AI enables resource efficiency and maximization.
Frequently asked questions
Q1. What are the cloud security challenges?
- Misconfiguration
- Insecure Interfaces/APIs
- Unauthorized Access
- Hijacking of Accounts
- Cyberattacks
- External Sharing of Data
- Lack of Visibility
- Malicious Insiders
- Denial of Service Attacks
- Data Loss/Leakage
- Data Privacy/Confidentiality
- Accidental Exposure of Credentials
- Incident Response
Q2. What are cloud security techniques?
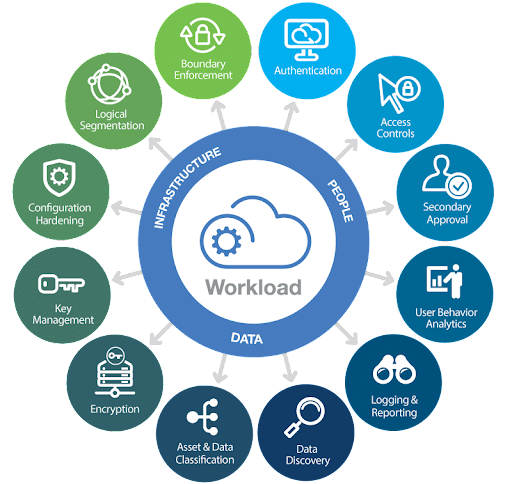
Source: Cloud security techniques
- Authentication software is primarily responsible for ensuring that an individual or computer is authorized to access resources in the cloud.
- Encryption refers to the process of encoding data into an unrecognizable format. Therefore, if a hacker accesses your data, you will need an encryption key to decrypt your data.
- Data integrity ensures that the data represents what we expect.
- There are many types of attacks on the cloud. To prevent some of these attacks, you can disable some port numbers in the cloud, install the latest antivirus measures, or use a firewall to stop the attacks.
Q3. What is cloud security architecture?
The cloud security architecture describes all the hardware and technologies designed to protect the cloud platform’s data, workloads, and systems. The development of a cloud security architecture strategy should begin with the blueprint and the design process and integrate with the cloud platform from scratch. Cloud architects often focus only on performance first and then try to add security later.
Q4. What are the components of cloud security?
The five cloud security components are secure architecture, compliance, due diligence, network monitoring, and a solid authentication protocol. As the number of attacks increases, cloud security is more important than ever. Cloud protection begins with a secure architecture that includes firewall placement and intrusion prevention systems. Organizations must adhere to their country’s data protection standards and perform due diligence. Cloud monitoring and visibility are key to the timely detection of attacks. The authentication system acts as the first line of defense against potential attacks.
Q5. What are cloud security standards?
Cloud security encompasses the technologies, controls, processes, and rules that integrate to guard your infrastructure. Cloud security standards provide a framework for building or strengthening cloud security and privacy strategies. You can then implement the tools, policies, and other resources needed to meet these criteria. For example, you can integrate automated compliance testing or cross-stack security and compliance integration solutions into your CI / CD pipeline to ensure that cloud security standards are met at all stages of your SDLC.















