Cloud computing received unprecedented success during the Covid-19 outbreak in 2020, and the trend continued after that, making it among the top most sought-after technologies. Most companies, from big to small, have shifted from physical IT infrastructure to cloud-based infrastructure as it offers a host of benefits, such as easy scalability, reduced costs, remote working, better reliability, boosted data security, increased revenue, and many more.

Disadvantages of Cloud Computing
By the end of 2022, global public cloud-based services end-user spending is expected to reach $ 494,654 million, and the trend will continue, according to Gartner. However, is cloud computing technology perfect? The answer is no. As we know, nothing is perfect in this world, and there are limitations to cloud computing that need to be resolved to make it work even more effectively. Let’s shed light on the disadvantages of Cloud Computing and suitable measures to tackle them so that business operations and delivery of services are not affected in any way.
Contents
What is Cloud Computing?
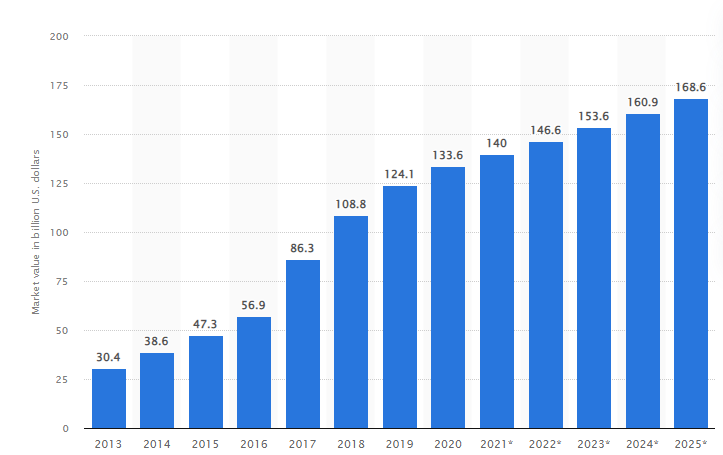
Cloud Market Size from 2013-2025
Cloud computing is an evolving technology that offers on-demand delivery of various IT resources through the internet. These resources include different tools and applications such as servers, data storage, databases, software, and networking. Instead of keeping all the files on hard drives or other storage devices, cloud storage allows data storage on remote databases. Users can access files and applications on the web from anywhere, securely. Some companies build their own cloud computing system, but most prefer to run their operations on the public cloud offered by top service providers like Amazon Web Services, Microsoft Azure, Google Cloud, etc. There is also a hybrid cloud computing model that includes both public and private clouds.
The worldwide cloud computing market share was $133.6 billion in 2021 and is expected to reach $168.6 billion by 2025. The cloud services market is forecasted to achieve a yearly growth rate of 4.8%. The different cloud computing functions include,
- Creating & testing apps
- Storage, backup, retrieval of data
- Data Analytics
- Video & Audio streaming
- Delivery of software on demand
Cloud Computing comprises three types of services
- Software-as-a-service (SaaS)
- Infrastructure-as-a-service (IaaS)
- Platform-as-a-service (PaaS)
There are numerous advantages and disadvantages of cloud computing that enterprises must be aware of so that appropriate countermeasures can be taken to minimize the disadvantages. The major benefits of Cloud Computing include,
- Cost Savings
- Better Security
- Data Loss Prevention
- Automatic Software Updates
- Competitive Edge
- Sustainability
- Flexibility
- Mobility
- Increased Collaboration
- Quality Control
- Disaster Recovery
Risks, Threats, and Vulnerabilities: Cloud Computing
Enterprises that use cloud computing services and applications either in-house or through cloud service providers (CSPs) can get into serious trouble if they are not fully aware of the risks, threats, and vulnerabilities of cloud computing.
Some of the major cloud computing risks, threats, and vulnerabilities include,
- Misconfigured cloud storage
- Data breaches
- Unauthorized access
- Insecure APIs
- Account hijacking
- Malicious insiders
- Cyberattacks
- Lack of visibility
- Data privacy
- Downtime
- Vendor Lock-In
- Security and Compliance
- Dependency on network connectivity in cloud computing
We must incorporate best practices for risk management in cloud computing to maximize its benefits and keep the risks and threats under control.
Drawbacks of Cloud Computing
Vulnerability to attacks
One prominent and most common cloud computing threat is data theft, as the company stores all critical data online in the cloud database. Unfortunately, a data breach is something even large organizations with a full-proof security system are unable to prevent. Although advanced security protocols are followed on the cloud, confidential data stored there is always vulnerable to cyberattacks from any corner of the world.
Network connectivity dependency
Network connectivity in cloud computing is crucial for reaping its benefits. This direct correlation means that any company that shifts entirely to cloud computing needs to have a fast and reliable internet connection to maximize the benefits of cloud computing. Even remote working is not possible without good internet to connect at the employee end, making network connectivity dependency a major limitation of cloud computing.
Downtime
Downtime is regarded as the biggest cloud computing risk of using cloud computing. The public cloud providers may face technical issues at times due to various reasons like natural disasters, power outages, low Internet connectivity, breakdown of data, etc. This can lead to a temporary or more extended downtime on the cloud platforms, depending on the severity of the technical issues.
Vendor lock-in
When there is a need to migrate from one cloud computing platform to another, an enterprise might face serious issues due to the differences between the two platforms. For example, when running applications and storing data from the previous cloud platform when migrating to a different one, there might be support issues and configuration complexities, and it may require modifications in the applications that can lead to additional expenses. In addition, cloud computing vulnerabilities can’t be ruled out when there is migration, and companies must take necessary precautions for the smooth transfer of applications and data to the current cloud platform.
Limited control
Cloud users might need to cope with limited control over their deployments. Cloud applications run on remote servers and are owned and managed by the service providers. This makes it challenging for enterprises to get sufficient control so that they can make changes to back-end infrastructure as and when needed.
Security and Privacy
Although cloud providers deploy the best security systems adhering to industry standards, storing critical data on third-party servers is one of the major security risks of cloud computing. Any protocol building involving data must consider security and privacy, especially when handling sensitive data. As these are constantly accessed remotely, there are chances of a data breach or some malware being used to corrupt the data. As a result, security concerns in cloud computing are always the deciding factor when it comes to choosing a third-party cloud service provider for any company.
Best Practices to Avoid These Risks
Cloud security includes all types of processes and applications that ensure an enterprise’s cloud infrastructure is protected against both internal and external cloud computing threats. As more enterprises are looking to shift their entire operations to the cloud, security becomes the number one priority to make it sustainable for a long time.
Cloud security is always evolving, but some of the best practices still remain the same, ensuring that cloud computing risks are prevented or mitigated as soon as they appear. Enterprises that are currently working on a cloud platform or planning to deploy one must follow the below best practices for minimizing the security risks of cloud computing are,
- Have a clear understanding of your shared responsibility model
- Ask detailed security questions and get clear answers from your cloud provider
- Implement an access and identity management solution
- Offer thorough training to your employees on using the cloud platforms
- Develop & enforce cloud security policies
- Ensure endpoints are secured
- Encrypt data both at rest and in motion
- Utilize intrusion detection & prevention technology
- Thoroughly check your compliance requirements
- Carry out audits & penetration testing
- Create security logs
Conclusion
Although there are limitations to cloud computing, like every other technology in the world, the benefits outweigh the risks, making it a necessity both now and in the future. The trick is to follow the best and most proven strategies for risk management in cloud computing and maximize the benefits that can take your enterprise to new heights in terms of customer service and revenue growth.
As we know, cloud computing is evolving, and with that, the complexities of the threats and vulnerabilities will also increase simultaneously. But if we manage to detect and mitigate cloud computing threats through best practices and advanced security systems, we can leverage the benefits of cloud computing and optimize each and every business operation, leading to higher productivity, better service delivery, and the creation of more revenue streams along the way.
The advantages and disadvantages of cloud computing make it dynamic and exciting at the same time, but with the right approach, the limitations can be turned into solutions that will help make cloud technology more efficient and relevant.
FAQs
- How do you manage the cost of cloud computing?
For effectively controlling cloud computing costs, it is imperative to analyze and manage cloud costs at all times. You can utilize cloud cost management tools to help identify issues that are creating more expenditures. Unplanned expenses frequently occur due to a lack of visibility with respect to current consumption patterns and historical trends. Also, nonstandard deployments, poor organization, or the lack of automated deployment can significantly increase cloud computing costs. Some of the top cloud cost management practices include,
- Visibility on Cloud Inventory
- Conduct Cost Analysis frequently
- Use controlled stack templates
- Deploy Role Based Access
- Install Automated Alerts & Notifications
- Keep a strict budget and stick to it
- Policy Based management
2. What are the fundamentals of security in cloud computing?
A: There are numerous methods that assist in successfully managing the security risks of cloud computing. The steps in combating cloud computing risks include firewalls, access control, obfuscation, penetration testing, tokenization, VPNs, etc. Don’t just blindly migrate to the cloud and perform risk management in cloud computing using the below tips,
- Understand your roles and responsibilities in the cloud environment
- Control user access
- Data protection
- Increase visibility
- Implement MFA (multi-factor authentication)
- Adopt a shift–left approach
- Secure credentials
3. What is Cloud Risk Management?
A: It is the process of securing, assessing, and managing all kinds of security risks of cloud computing. It involves an assessment of your enterprise’s cloud footprint. The Risk Management procedure requires an evaluation of the enterprise’s competency to deliver products and services within a fixed timeline and showcase a commitment to security and privacy levels. Cloud Risk Management assists organizations in understanding cloud computing vulnerabilities. It helps enterprises make useful security modifications and align their business operations accordingly. Cloud risk management also helps organizations make informed decisions on cloud computing services when considering outsourcing. If done right, cloud risk management helps improve operational efficiencies and drive business growth.
4. Why Cloud Security assessment is important?
A: A cloud security assessment provides enterprises a sense of relief that their assets and networks are correctly configured, sufficiently secured, and not the subject of an ongoing cybersecurity attack. The advantages of cloud security assessment include,
- Minimized risks due to accidental misconfiguration
- Reduced risk from missing notifications
- Boosted resilience
- Better account management
- Detection of the previous compromises
Cloud Assessment is performed through the below steps
- Documentation review & interviews
- Automated & manual testing
- Generation of Recommendations
- Presentation















