Everyone who runs internal systems, whether physical or virtual, to support their company’s demands for network security must be aware of their responsibilities. There is no substitute for network segmentation when it comes to protecting your data.
Segmentation becomes more critical as the design becomes more complex. Businesses that rely solely on software as a service (SaaS) or that don’t employ IT services are the only ones that won’t need network segregation.
Before we get into the specifics of how to segment a computer network, let’s define what it is first.
Contents
Network Segmentation: What is it and how does it work?
Network segmentation is a network security approach that divides a network into smaller, independent subnetworks. It allows network teams to compartmentalize security controls and services for every subnetwork.
In a network segmentation, a physical network is subdivided into several logical networks. Then, controls are added to each network component once it has been broken down into smaller, more manageable units.
How does it work?
If you’re looking to construct various distinct networks within a bigger network, network segmentation is excellent. The same level of trust protects specific categories of applications or endpoints in these segments.
Network segmentation can be accomplished in a variety of ways:
1. Perimeter-Based Segmentation
Perimeter-based segmentation divides a network into trusted and untrusted parts based on the trustworthiness of the network’s perimeter. The outcome is a flat network with low internal network segmentation that has few limits on internal resources. Fixed network points are used for filtering and segmentation.
Network performance was initially intended to be improved through virtual local area networks (VLANs), which evolved into security tools over time but were never intended to be used. As VLANs lack intra-VLAN filtering, they provide a wide range of access to the network.
A firewall is a standard method of securing the perimeter of a network. If you’re looking to manage network traffic moving north-south but still allow for communication between segments, this is the right tool.
2. Network Virtualisation
There are now many businesses with a range of network areas that require segmentation at various network points. In addition, the number of endpoint types and trust levels that the network must handle has increased.
Because of this, segmentation based on the perimeter is no longer adequate. There are no clear boundary points between the cloud, BYOD, and mobile due to these technologies. Security and performance will improve if we move further into the network with greater segmentation. Even more network segmentation is needed because of today’s east-west traffic patterns. Using segmentation to the next level is made possible by network virtualization.
In its simplest form, network virtualization provides network and security services independent of the physical infrastructure. Network virtualization is an essential factor in promoting effective network segmentation since it makes segmentation possible throughout the entire network, rather than simply at the perimeter.
Network Segmentation Example:

Subnetwork or subnet segmentation is a preventative measure of security breaches by breaking a big network into smaller subnets or networks.
Network segmentation aims to restrict communication between subnetworks to reduce illegal access to devices, data, and applications. Therefore, it is critical to Zero Trust that network segmentation is implemented since it reduces the chances of lateral movement within a network.
Each subnet on a segmented network serves as a virtual LAN (VLAN). Subnets can be interconnected via security policies, which specify which users, services, and devices are allowed to do so. The most priceless assets will be protected by the most stringent security measures.
Network segmentation examples:
Using an internal firewall as a network segmentation example is one way to do this. Network experts can divide the two networks on either side of the firewall into their subnetworks. For example, data can be inspected for harmful code in the first subnetwork environment before traveling through the firewall to the other side of the network.
Network segmentation can be an invaluable tool when it comes to routing data. Engineers may limit the types of data sent through a particular network segment to improve security or reduce the amount of traffic that puts a strain on the network’s hardware or consumes additional resources.
Other network segmentation examples include an attempt to move about the network by someone who has gained access to your network to access and exploit sensitive data. An attacker can easily access the entire system through a single point of entry if the network is flat (without intermediary devices like a bridge or router).
When it comes to today’s modern and sophisticated interconnected companies, flat networks are particularly vulnerable because of their lateral access between systems.
On the other hand, malicious traffic will not have rapid access to the entire ecosystem if the network is divided. As a result, attackers will be confined to the initial area they infiltrated, giving IT time to detect the breach and mitigate its impact.
Network Segmentation Policies
Network segmentation helps a corporation minimize its cybersecurity risk while adopting a zero-trust security policy. Moreover, network segmentation creates zero-trust network barriers.
For a long time, just the network perimeter could be secured. Using these steps, you can successfully segment a company’s network.
1. Determine Valuable Information and Assets
The value of an organization’s data and assets isn’t the same across the board. To keep things running smoothly, some systems, like the customer database, are necessary. A printer is an example of a tool that’s useful but not critical to the company’s operation.
2. Apply Labels to Each Asset’s Classification
Both the sensitivity (i.e. the public to be highly restricted) and the sort of data that an asset includes should be considered when assigning labels to these assets. In addition, complying with requirements like the Payment Card Industry Data Security Standard (PCI DSS) aids in the formulation of segmentation strategies.
3. Map the Network’s Data Flows
By dividing the network into discrete sections, network segmentation aids in enhancing network security. An attacker will have a more difficult time moving laterally through the network once they have established a foothold.
4. Identify and Classify Asset Subgroups
In a networked environment, certain assets have similar functions and communicate often. Therefore, it would be impossible to sustain regular operation if these systems were isolated from one another, as several exceptions would have to be made.
5. Deploy a Gateway for Segmentation
Determining segment boundaries is critical, but the organization will receive little advantage if they are not upheld. Therefore, installing a segment gateway is required to enforce access controls on each network segment.
6. Create Policies for Access Control
Depending on the segment, unlimited traffic flow between assets may be allowed. On the other hand, inter-segment communications must be monitored and adhere to access control policies by the segment gateway.
If we consider the principle of least privilege, an application segmentation should only have the rights necessary to perform its duties.
7. Ensure Regular Audits and Reviews
Network segmentation is nearly complete after defining micro-segments, deploying the segmentation gateway, and developing and enforcing access control policies. However, the network segmentation policy definition isn’t a one-time endeavor.
8. Automation
Defining a network segmentation policy can be a major undertaking for large networks. It may be quite impossible to carry out all of these tasks by hand.
Types of Network Segmentation
1. Network Segmentation

Segmenting networks via VLANs or subnets has long been standard practice. Smaller network segments can be created by creating virtual local area networks (VLANs), which connect all hosts virtually to one another.
Subnets use IP addresses to divide a network into smaller sections that can be interconnected with the help of networking equipment. As a result, these methods improve network performance and prevent attacks from propagating beyond a single VLAN or subnet.
Approaches such as this face two major hurdles. Networks are often re-architected to fulfill segmentation requirements. The difficulty of writing and managing thousands upon thousands of ACL rules that reside on network devices to establish subnets is the second issue.
2. Firewall Segmentation
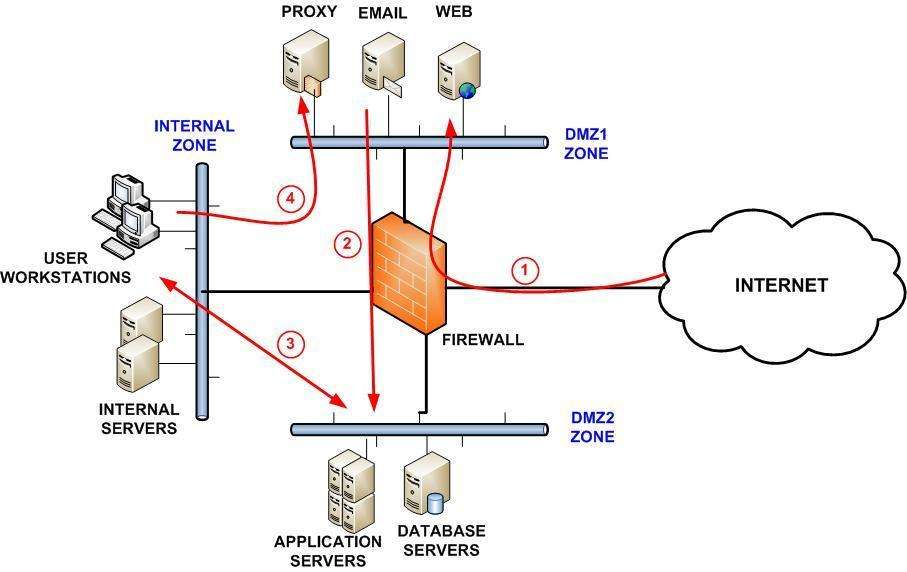
Firewalls can be used instead of the network to ensure segmentation. For example, an internal network or data center can be partitioned into functional zones by deploying firewalls to isolate them from each other. This prevents attacks from propagating to other functional areas. An example of this would be to separate engineering applications from financial ones. PCI data, for example, is a classic example of a sensitive area to secure.
3. Segmentation with SDN

SDN relies on centralized controllers isolated from the network’s physical hardware to provide higher network automation and programmability. For example, SDN network overlay implementations can be used to build policies that filter packets via a distributed set of firewalls to achieve segmentation.
When applications do not fit within network boundaries, the high complexity required for successful micro-segmentation is a concern. As a result, SDN focuses on network policies rather than security visibility into workloads and application flows that other techniques address.
4. Micro-Segmentation:
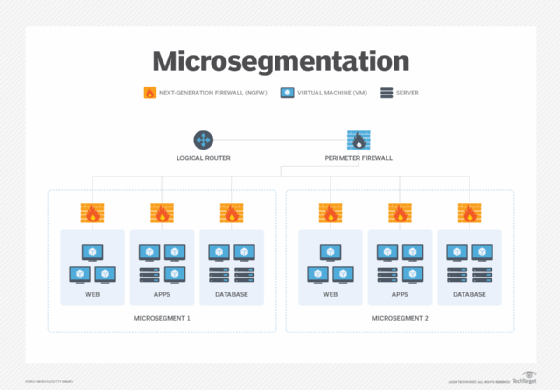
It is possible to achieve segments in a computer network without utilizing subnets or firewalls, but this is not the only option. Each data center or cloud workload operating system has a native stateful firewall, such as Linux’s IP tables or Windows’ Windows Filtering Platform.
All traffic, other than that which is permitted, is blocked by this strategy. Security segmentation is another name for micro-segmentation, also known as host-based segmentation.
By using host telemetry data, cloud and on-premise environments and apps may be segregated. In addition, maps can be used to create an automated segmentation method. Instead of IP addresses or firewall rules, policies use labels. The ability to control segmentation at the process level is an added advantage.
Moreover, with the help of micro-segmentation security, data centers can be divided logically down to individual workload levels and then defined and provided with security controls and services on a per-segment basis.
The Benefits of Network Segmentation

1. Better Network Performance
It’s easier to monitor the segmentation of the network and detect suspicious activity when more checks are in place. Moreover, advanced monitoring can reveal the source and scope of a problem.
Administrators can look for patterns in harmful activity by keeping an eye on log events and internal connections. As a result, administrators may better defend high-risk areas by understanding how attackers operate.
2. Limit Cyberattack Damage
Hackers can only access a single subnet on a split network. Therefore, it can take some time to get a handle on the remainder of the network.
Admins have the opportunity to strengthen the security of other segments in computer networks while hackers attempt to infiltrate other subnets. Once the problem has been contained, administrators can concentrate on the breached portion.
3. Protection of vulnerable devices
It is easier to restrict access to your most sensitive data and systems if you have robust network segmentation. If a user’s access credentials are compromised or abused, this can be a lifesaver in securing that information. In other words, application segmentation helps you defend your company from insiders and outsiders.
4. Reduced Congestion
By restricting user access to a single network segment, segmentation helps guard against insider threats. The “Policy of Least Privilege” is given to this type of security. By limiting access to essential parts of the network to a select few, you reduce the opportunity for hackers to compromise crucial systems.
People are the weakest link in the network security chain. Hence, the Least Privilege Policy is essential. An intruder can’t access key resources if the user’s login credentials are compromised or misused in the segmented network.
5. Containing Network Problems
To minimize the damage caused by a network breach, good network segmentation can help keep attackers from breaking out of the system until you’ve confined and shut them down.
Segmented networks protect both end-users and devices, as well as the segments themselves, from threats that originate at the network endpoints.
FAQs
1. Why is network segmentation important?
A new perspective on network segmentation is emerging due to increased cyber risks and cyberattacks. As part of a security strategy, businesses and organizations throughout the world are using network segmentation as a disincentive to hackers.
Traffic efficiency is one of the perks of segmenting a network. A “packet” is a small piece of data sent from one computer to another containing both the communication content and information about the sender and receiver.
As a result, your network will be able to handle higher traffic volumes and will be better equipped to handle future growth.
2. What is network segmentation in cyber security?
Network segmentation provides distinct security services for each network segment, increasing control over network traffic, enhancing network performance, and enhancing security.
First and foremost, there must be an increase in security. In terms of security, we all know that your weakest connection is your most vulnerable point. This is because the attack surface of a big flat network is invariably large. Smaller sub-networks, however, limit the attack surface and hamper lateral mobility when a large network is broken into smaller sub-networks.
For example, segmentation guarantees that malware in one section does not spread to other systems. Creating segments restricts an attack’s distribution and minimizes the attack surface.
3. How do you segment a network?
In network segmentation, a bigger network is divided into smaller ones. Firewalls, virtual networks (VLANs), and other approaches can be used to separate networks.
Ransomware or hackers can’t propagate across the network if safeguards based on segmentation are in place to keep the network from being infected.
Segmenting a network is an effective defense against viruses and malware that propagate on their own, such as ransomware. If a user double-clicks on a faulty link in a section of your network that has been logically segmented, the damage will be restricted to that section of the network and not spread to other sections.
4. What are the effects of network segmentation?
Network segmentation can help protect your internal network assets’ most sensitive data. Adding a layer of protection between your network’s critical data servers and the rest of the internet can greatly lower your chances of experiencing data loss or theft.
Segmenting the network is also a good idea since it prevents illegal traffic or attacks from reaching parts of the network that we don’t want to be accessible. When a network is segmented, it is divided into smaller networks, each of which is referred to as a “subnet.” Subnet traffic can be allowed, disabled, or blocked depending on criteria.
5. What is network segmentation testing?
A segmentation check consists of a set of penetration tests to verify that networks with lower levels of security cannot communicate with those with higher levels of security. (typically the CDE). Your company’s segmentation is being tested to ensure that it is secure and that the controls function effectively.
Penetration testers verify segmentation by doing a port scan (typically using Nmap) inside the network without access to the CDE. A network segment is considered successfully segmented if no IP addresses can be found inside it from networks that have access to the CDE (or are isolated from the CDE).
6. Is VPN a segmentation of the network?
Extending private networks across public networks, virtual private networks (VPNs) allow computers to communicate with each other as if they were directly linked to the private network.
A virtual private network (VPN) improves the private network’s functionality, security, and management. Virtual private networks (VPNs) allow distant workers to access resources unavailable on the public Internet. A VPN connection does not come pre-encrypted, but it is a frequent practice.
A dedicated circuit or tunneling techniques are used to establish a virtual point-to-point connection over an existing network to create a VPN.
7. What are the 3 main purposes of network segmentation?
The 3 Main Purposes:
1. Security
The attack surface of a single logical network can be greatly reduced by segmenting network resources into separate networks, each with its own hardware.
2. Visibility
Administrators benefit significantly from the near-perfect efficiency and resource utilization that comes with properly segmenting a network. Visibility in a specific market segment is highly specific, so this is the case.
3. Response
One additional benefit is that an admin can respond much faster than a pooled network, especially one with a shared server farm, to an event because of the admin’s superior network visibility.
8. What is a network segment diagram?
It is known as network segmentation, and it involves splitting a network into numerous subnets or segments, each of which operates as its own independent micro-network. This independent micro-segmentation network is known as network segmentation. By segmenting a network, administrators can manage traffic flow between different subsets of the network according to increasingly specific policies.
A company may choose to segment its network to boost performance, improve monitoring activities, localize issues that arise with technicians, increase network security, etc. A network segmentation diagram offers a graphical picture of the process used to divide the network into its constituent parts.
9. Is network segmentation a PCI requirement?
PCI network segmentation is a critical security strategy for any company that wants to protect its cardholder data while reducing its PCI DSS compliance scope.
In “flat” networks, card-processing systems are integrated with back-office software. Compliance with PCI DSS must be ensured across the entire network in these circumstances. This might greatly increase the amount of work required to secure your business’s network.
As a result, many firms continue to employ flat networks despite their inherent security flaws. However, it’s important to remember that this way of thinking might lead to expanded PCI scope and security threats.
10. What are segmentation controls?
Segmentation is the process of separating systems based on the degree of security they require by adding additional safeguards. For example, segmentation can keep PCI DSS in-scope systems separate from PCI DSS out-of-scope systems. Logical controls, physical controls, or a combination of the two can be used for segmentation.
A few examples of segmentation methods used to reduce the scope of the PCI DSS are blocking traffic between out-of-scope networks and the CDE, configuring networks to block communications between different systems or subnets, and implementing physical access controls.
11. Is DLP a PCI requirement?
Yes, using PCI DSS Requirement 11’s Data Loss Prevention (DLP) technologies, companies can test their data protection solutions’ effectiveness by securing sensitive data through automated and human scanning.
Using Data Loss Prevention (DLP), system administrators can closely watch how their data is being used and transferred. Because of this, a PCI DSS Data Loss Prevention solution is a necessity.
In addition to these features, DLP software monitors network traffic, guarantees that the computer is utilized within the confines of predetermined regulations, and controls email. In this manner, it is possible to prevent data leakage.
12. How do I become PCI compliant?
Step 1: Remove key authentication data and minimize data retention
To mitigate the effects of a security compromise.
Step 2: Secure network systems and respond to a breach.
Block and secure access points that are often breached.
Step 3: Secure payment card apps.
Payment application security and controls are addressed
Step 4: Manage and supervise access to your systems
Monitoring who has network access and what they do when connected.
Step 5: Ensure the security of cardholder data
Storing primary account numbers (PANs) in a secure manner.
Step 6: Complete compliance efforts and verify the presence of all controls
Document your organization’s regulatory compliance requirements.
13. Is Payeezy PCI compliant?
First Data Payeezy Gateway Payment Pages is a non-storing, “hands-off” solution that perfectly meets Payment Card Industry Data Security Standards (PCI-DSS).
Its Payment Pages limit merchant exposure to cardholder data while reducing the need for SSL certificates. The importance of PCI compliance is only underscored because it is a legally mandated requirement.
Payeezy Gateway Payment Pages can be customized to meet the merchant’s needs. Colors, logos, and phrasing can be supplied to Payeezy Gateway in HTML format so that the cardholder has the same user interface during payment as when they are shopping on the merchant site.
14. What qualifies as a PCI?
PCI DSS is a set of security guidelines meant to ensure that all businesses that take, handle, store, or transport credit card information maintain a secure environment.
Paying with a credit card may be a risky business, which is why the Payment Card Industry Security Standards Council was established on September 7th, 2006, to oversee the development of PCI Security Standards.
As a result of the efforts of the main payment card companies, the PCI SSC was established to administer and monitor the PCI DSS (Visa, MasterCard, American Express, Discover, and JCB).
15. Is it forbidden to record credit card numbers?
You should never physically record any credit card information unless your business procedures explicitly require it. Without the cardholder’s permission, never obtain or disclose any type of credit card information, including the partial sixteen (16) digit number.
The physical security of paper and electronic media, such as removable electronic media, computers, reports, receipts, or faxes, must include all records, including cardholder data.
Credit card processors should only be able to access locked drawers and safes. In addition, all paper and electronic media should be accounted for in a media inventory, and inventory logs and audit trails should be kept.















